A new research by Symantec talks about the dangers of Media File Jacking, a type of attack undertaken by cybercriminals to target media files, which are sent through instant messaging apps like WhatsApp and Telegram, and are stored in external storage of Android phones. The criminals can take advantage of a flaw that exposes these media files and they can then be manipulated by malicious actors, Symantec’s Modern OS Security team has found. The researchers say that this vulnerability stems from the (very short) lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume.
“This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge. If the security flaw is exploited, a malicious attacker could misuse and manipulate sensitive information such as personal photos and videos, corporate documents, invoices, and voice memos. Attackers could take advantage of the relations of trust between a sender and a receiver when using these IM apps for personal gain or to wreak havoc,” Yair Amit, VP and CTO, Modern OS Security, and Alon Gat, Software Engineer at Symantec, said in a blog post.
What’s concerning is that the Media File Jacking is prevalent at a time when IM apps offer, or claim to offer, immunity such as end-to-end encryption on their platforms. The team says that the end-to-end encryption is an effective mechanism to ensure the integrity of communications, but it isn’t enough when a threat expands to the media shared and stored in a mobile device. Researchers found that attackers may be able to successfully manipulate media files by taking advantage of flaws in the apps, that occur before and/or after the content is encrypted in transit. Further, the team said media files stored on external storage are more vulnerable.
“Android apps can store files and data in two storage locations: internal and external storage. Files saved to internal storage are accessible only by the app itself, meaning other apps cannot access them. Files saved to an external storage public directory are world-readable/writeable, so they can be modified by other apps or users beyond the app's control,” the blog reads. By default, WhatsApp stores media files received by a device in external storage, and by contrast, in Telegram, this happens only if a user enables the “Save to Gallery” feature.
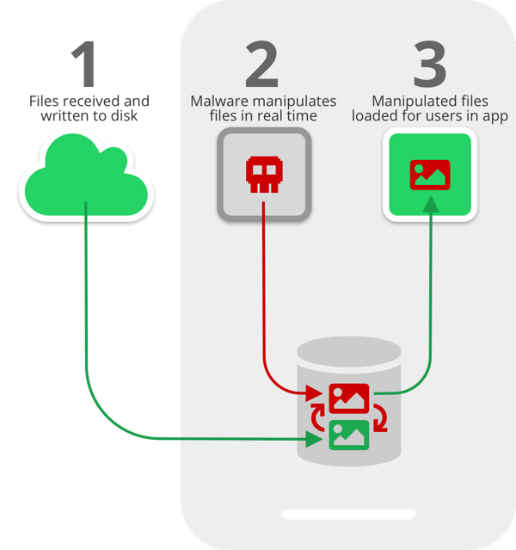
As seen in the image above, in the time between when files are first received on a device and written to the disk (STEP 1), and when they are loaded for users to consume via the apps (STEP 3), malware can instantaneously analyse and manipulate the files (or just replace them with the attacker’s chosen files) for malicious gain (STEP 2).
The thumbnail that appears in the notification that users see will also show the manipulated image or file, so recipients will have no indication that files were changed. What’s terrifying is that the data can be manipulated on WhatsApp both when sending files (which means the attack is launched on the sender’s device) and when receiving files (that is, the attack is happening on the receiving device). (See video below)
Even the Android developer documentation mentions the threat of saving files on external storage. “Internal storage is best when you want to be sure that neither the user nor other apps can access your files.” On the contrary, “external storage is the best place for files that don't require access restrictions and for files that you want to share with other apps or allow the user to access with a computer.”
from Latest Technology News https://ift.tt/2XMKUoo

No comments:
Post a Comment